A boringly deep analysis of a very complex VBS Malware dropper

LOLSnif is a new(ish) variant of the common trojan Ursnif.
Here, we take a look at the very complex and heavily encoded/obfuscated script that drops the malicious DLL on the victim machine.
Apologies if it gets a bit boring, I’ve crammed in too much stuff here. Feel free to skip sections that are of less interest.It all starts the usual way, phishing email brings in a link that serves the initial script. The script itself has the malware in it, which is dropped on the victim machine on successful execution.
This script has a lot of anti-analysis, anti-sandbox features that are clever and heavily encoded which makes them well-hidden.
Let’s take a step-by-step look at this malware:
There are more than 500 lines of code in the script and most of those lines have thousands of chars in them. This is a very long script, based on those numbers alone.
A lot of that is garbage, as is common with scripting malwares. What makes this one more complex than your average malware, is the lengths this author(s) has gone to in order to hide the code and make it hard to analyse.
For the purpose of this analysis (as with most of my work), we will analyse it dynamically and we’ll be clever in our approach. We will disable the anti-analysis features one by one and then make the malware execute the way we want. We will then record all the relevant actions and examine the results to form a complete analysis for Incident Response.
Anti-Sandbox features
This malware has a few tricks that allow it determine if it’s being executed in a sandbox — these are highly effective tricks and I can confirm that it evades analysis by major sandboxing solutions available in the market.
Cores
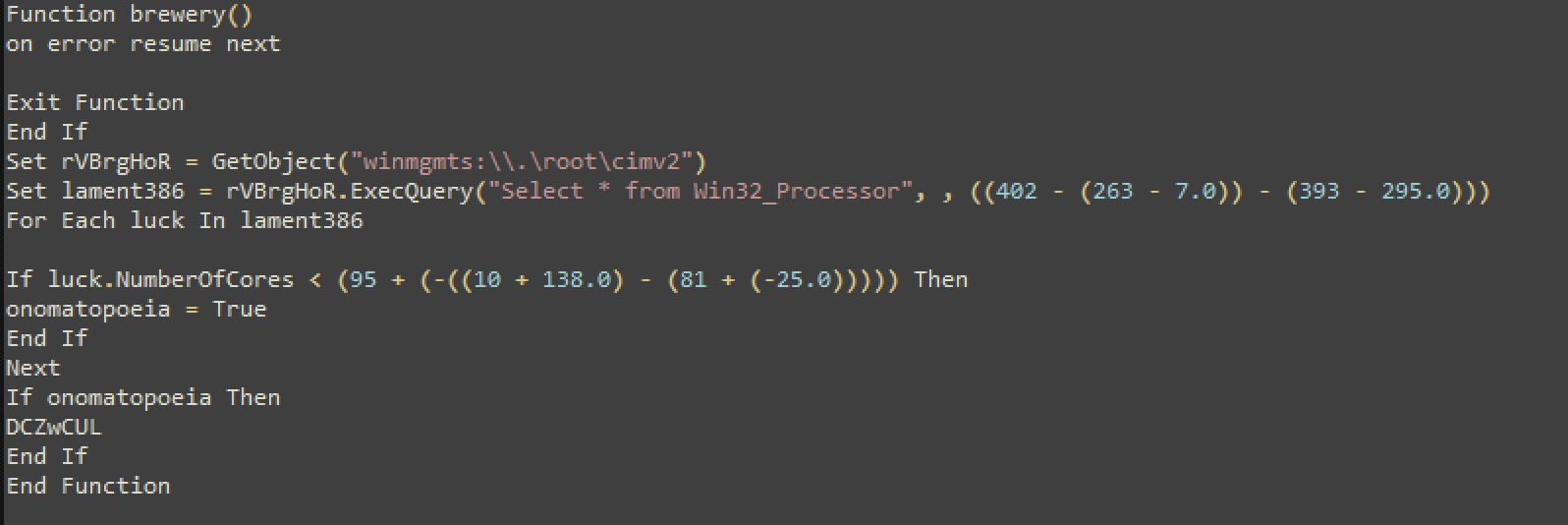
Let’s take a look at the function above.
The malware creates a WMI instance to query information in the cimv2 category for the local machine. This can be used to run queries on WMI, which is structured in classes.
Next, it uses a select statement to extract all info from the Win32_Processor class (table) and then goes ahead with querying the ‘NumberOfCores’ field.
The malware is trying to query the number of cores on the victim machine. Once it has that number, it runs it against am If statement:
If luck.NumberOfCores < (95 + (-((10 + 138.0) - (81 + (-25.0))))) Then
onomatopoeia = True
End If
Next
If onomatopoeia Then
DCZwCUL
End IfFrom the code snippet above, (95 + (-((10 + 138.0) — (81 + (-25.0))))) equals ‘3’.
So if the number of cores is less than 3, the condition is ‘True’. If true, the program runs the function ‘DCZwCUL’, which (we’ll see later) exits the program. It gives you a fake message about a missing ‘MSVCR102.dll’ which in reality doesn’t exists (try googling it).
Tip: Increase the number of cores to your VM to 4 or more and you'll bypass this feature. Memory
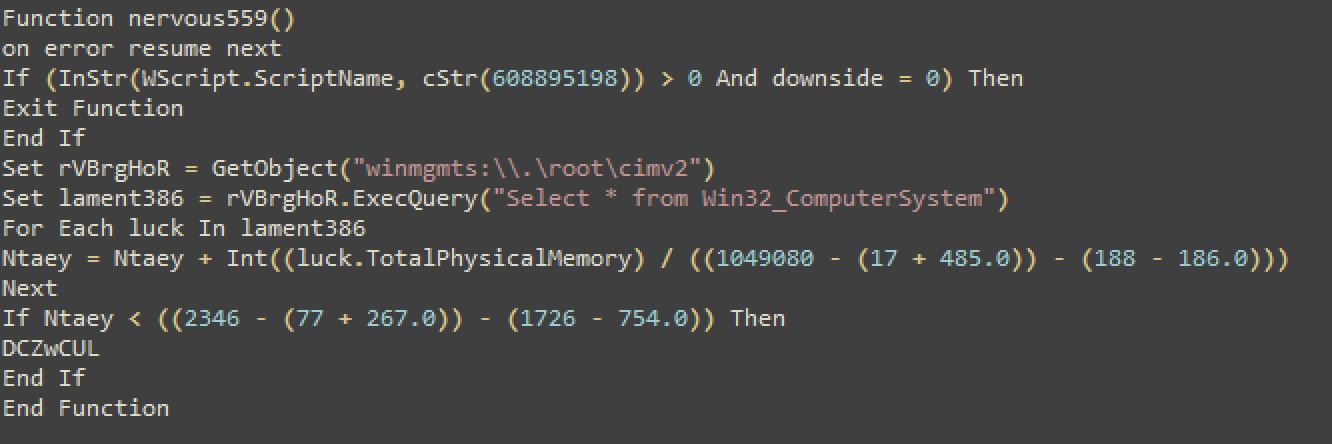
In this function, the malware tries to query the physical memory of the victim machine. It again uses the WMI classes for this purpose.
This time it queries the ‘Win32_ComputerSystem’ field.
If the physical memory is less than 1030 Mb, it terminates execution.
Tip: increase the memory of your VM to more than 1030 and you'll successfully bypass this feature. Common Analysis Tools
Personally, I like this list of common tools these malware authors use for anti-analysis techniques. I get to see a few new ones every now and then and I add them to my arsenal :)
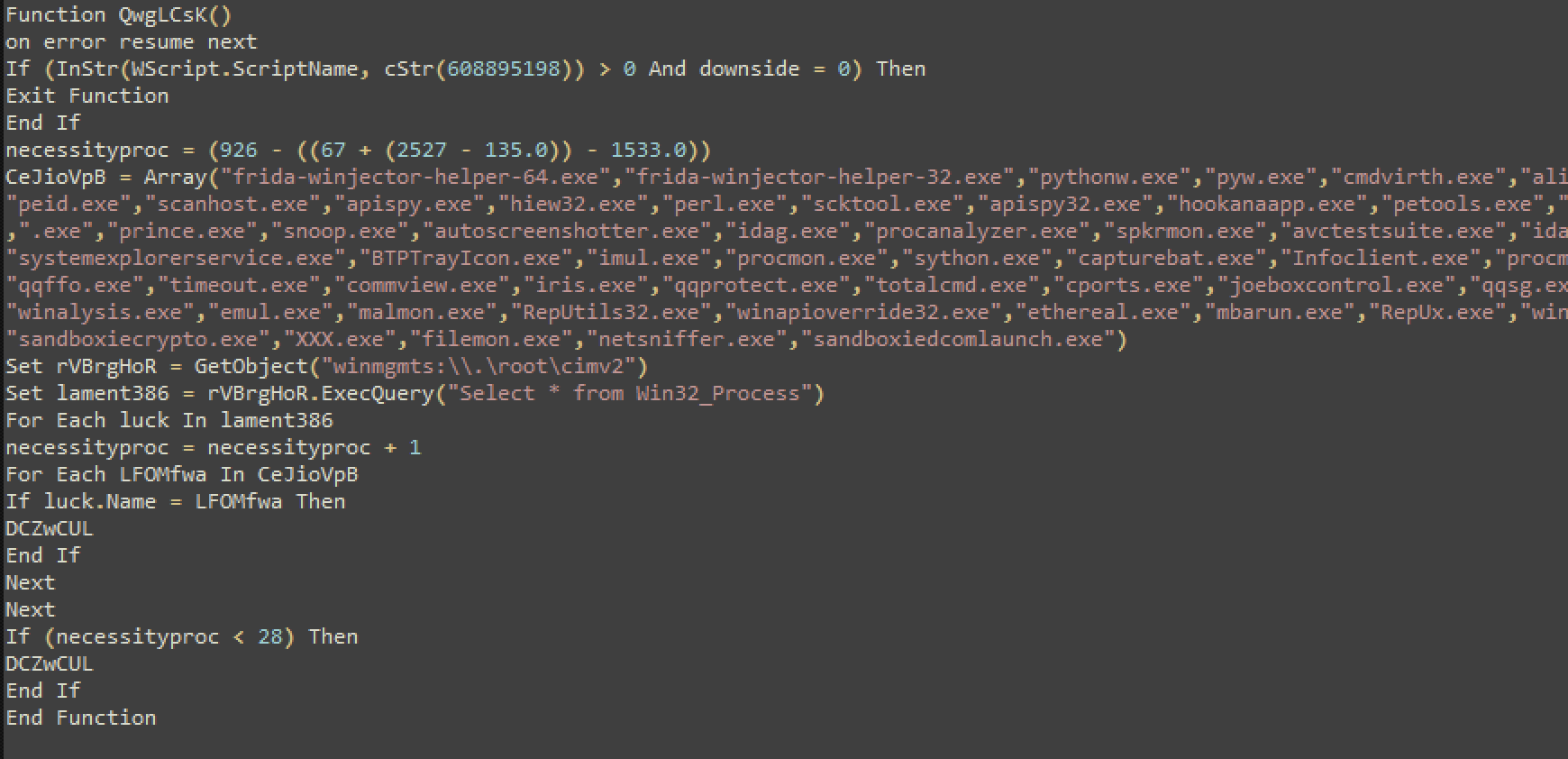
As you can see, the list above is quite comprehensive. Basically, the malware checks if you’ve got any of these tools running on your analysis machine and if it finds any of the ones listed in the function’s array, it terminates execution.
This function works flawlessly. I tested it by running a couple of these tools on the machine (procmon, procexp) and it identified those and terminated the program.
Tip: You can have these tools on your analysis machine, just make sure they are not running at the time of analysis - most of these are portable executables. I've written this quick script that tells you if any of these are detectable on your system. Run this script and see if any of these are detected. You'll have to terminate the detected tools to bypass this feature. https://github.com/vithakur/scripts/blob/master/sandbox_tools.vbs
Logical Volume Size

Another trick the malware uses is the size of the logical volumes on your analysis machine. In the above code snippet, you can see that the malware terminates execution if the size is less than 60 Gb. Most VM’s are less than that (especially in commercial cloud-based sandboxes).
Tip: If you can have a vm with a logical volume size of more than 60 Gb, you'll be able to bypass this feature completely. Number of files in certain folders
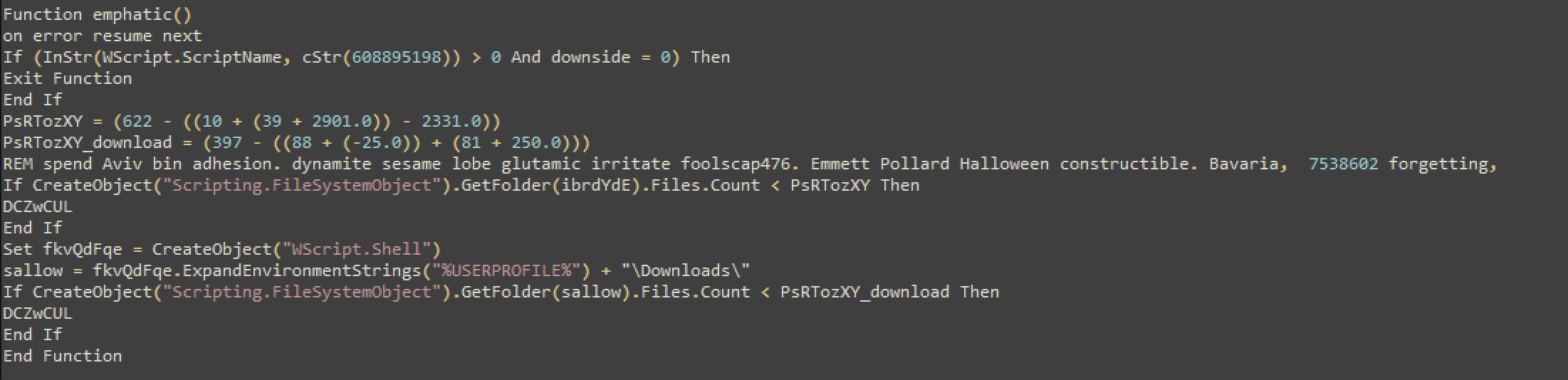
This is another neat trick by the authors. The malware checks a couple of directories to see how many files are in them to make sure it’s not an analysis machine the malware is running on.
The two directories it checks are:
\temp\\Downloads\
Here’s how it works:
The function declares two variables, to be used for comparison purposes later in the function.
PsRTozXY = (622 — ((10 + (39 + 2901.0)) — 2331.0))
(622 — ((10 + (39 + 2901.0)) — 2331.0)) = 3
PsRTozXY = 3
PsRTozXY_download = (397 — ((88 + (-25.0)) + (81 + 250.0)))
(397 — ((88 + (-25.0)) + (81 + 250.0))) = 3
PsRTozXY_download = 3
If CreateObject("Scripting.FileSystemObject").GetFolder(ibrdYdE).Files.Count < PsRTozXY Then
DCZwCUL
End IfibrdYdE refers to another function in the program:
Function ibrdYdE()
ibrdYdE = CStr(WScript.CreateObject(“Scripting.FileSystemObject”).GetSpecialFolder(((16 + (-11.0)) + (-((81 + (-49.0)) + (-29.0))))) + “\”)
End FunctionibrdYdE returns the special folder — ‘\temp\’ based on the function above.
GetSpecialFolder(((16 + (-11.0)) + (-((81 + (-49.0)) + (-29.0))))) + “\”)‘(((16 + (-11.0)) + (-((81 + (-49.0)) + (-29.0)))))’ = 2; 2 returns ‘\temp’
So, if there are less than 3 files in the ‘temp’ folder, terminate execution.
The second folder is the \Downloads\ folder, which is easier to see in the code itself:
sallow = fkvQdFqe.ExpandEnvironmentStrings("%USERPROFILE%") + "\Downloads\"Again, if there are less than 3 files in the Downloads folder, terminate execution.
Tip: Just put some random files in the Downloads folder, the malware just checks the number of files not the type of files or extensions. In the 'temp' folder (c\users\yourUser\appdata\local\temp) there should be more than 3 files usually by default.So, as you can see, quite a few anti-analysis, anti-sandbox features in this malware and all well-written.
Terminate Function
Now that we’ve had a look at all the anti-analysis functions in the malware, let’s quickly take a look at the function that is used to terminate execution of the malware.

From the code above, you can see that once the function is called, it calls three other functions and then terminates the program using ‘WScript.Quit’
The first function it calls is Crete():
This function doesn’t lead to anything, no requests are made.
The second function is kZDlOhis():
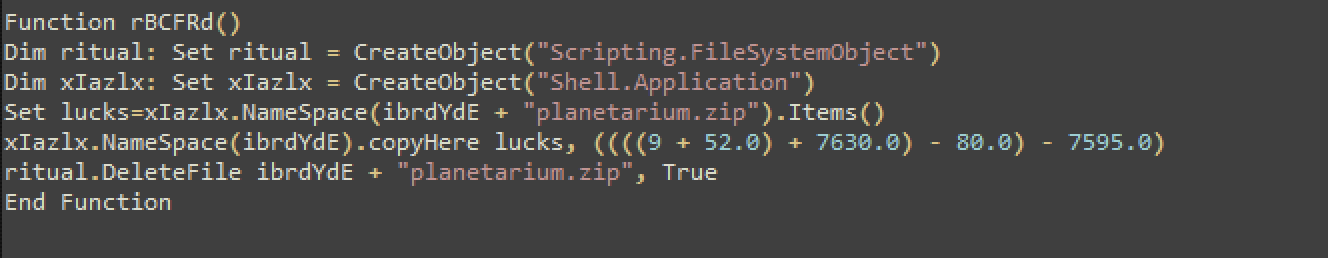
This function deletes the malware from the temp folder.
The last function is frank():
This function displays a misleading message, about a missing DLL that actually doesn’t exists, its a made-up file.
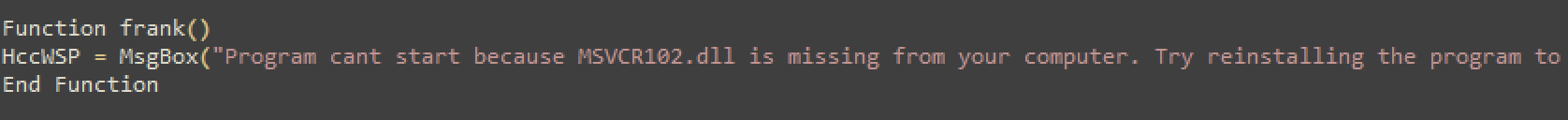
After this, the program terminates.
Execution after bypassing the anti-analysis checks
Now that we know how to bypass the anti-analysis checks, let’s take a look at how the malware actually executes.
This function does most of the work for the malware:
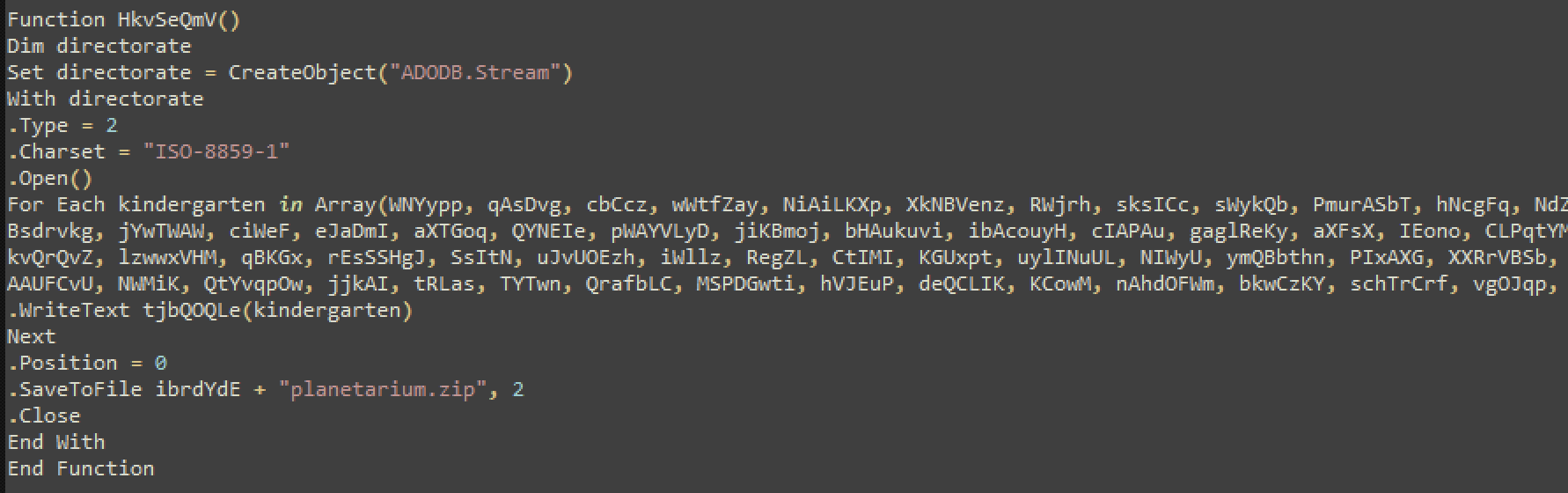
What’s happening in this function is this:
- Create the Object ‘ADODB.Stream’ — which in this case is used to write the binary data (the actual malware DLL) to the disk.
- Define the Charset of the data to be written
- Read through all the arrays supplied in the script with the binary data
- Write all that data to the file “planetariam.zip” using the ‘SaveToFile’ function
- Position is ‘0’ which means, re-write if file already exists
- Close the file
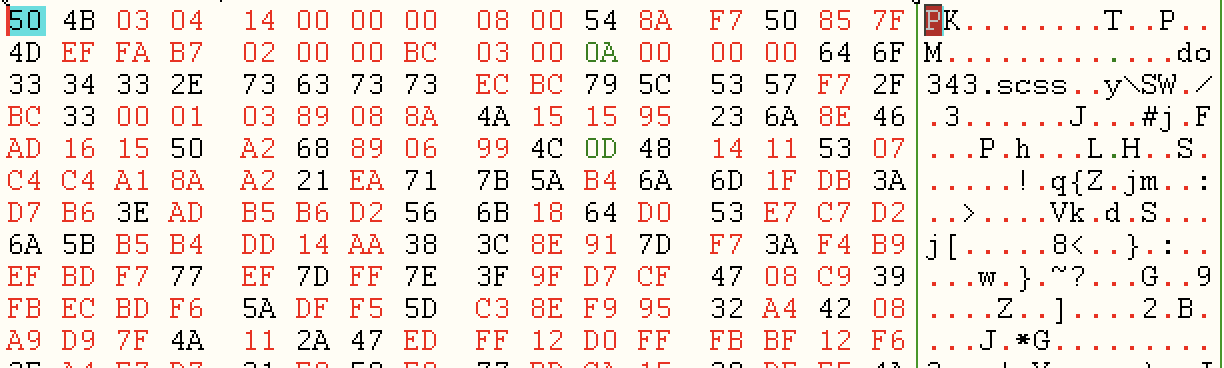
As you can see, all the values in Array are the arrays in the script, with the data to be written. Here’s an example:

This is the function that loads the DLL and executes it:

As you can see, it uses rundll32 to load the malicious dll. The malicious dll is ‘do343.scss’.
The malware also creates a URL file in the temp folder — this can be used as an IOC. It is linked to adobe.com

Malware DLL
Now that we know how to bypass all the anti-analysis techniques this malware uses and how to execute the malware in our analysis machine, let’s get to the final DLL that is the malware LOLSnif.
Among other commonly seen malware functions, this malware also reaches out to the C2 and tries to post the victim machine information.
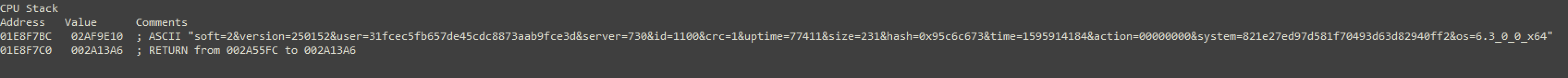
The DLL in this case works with DGA as we can see with all these requests that are being made:

Conclusion
The dropper for this malware is very complex. The authors have gone to great lengths to make it as hard as possible to analyse the code. There are layers and layers of encoding and obfuscation. To analyse it, you need to peel back each layer one by one, right to the end where it reveals the final payload, the malicious DLL.
Appendix
IOC:
At the time of this publishing, these are some of the Hashes for the LOLSnif DLLs:
9d55833324c088cf385ce6ae914ef21a
e65c0ac2d6964f5866eb9eddf8654f3f
654121216d3c75c83ef202785d5cc0ef
894877146bb0b8ea8adf0ee26e52c1d7
4549708f2a9c381890a5558b2036bc49
dcf79f6af5b4b2b9d46b8a4e0b09b7bd
faa84b171f792d7154d9e38e94199100
948e548aed01218c784b767b91504d18
048b1b3e0781ab1a2f93b0e27644fde0
28b17df90fb856d7e4540ac799094675
057065c30188f1c4c7974946acade6da
52b26eff6f2d5e2763fad705c4204016
059514bbe7fcbe147cdd0ece92172f66
e6be61c83d5d47576963a26f2301c08a
0078f7e4b72461c7e16179c619c15ad8
3f1c0646141e053865a4214108c74068
3b98f77f08f7849e84634b36b77b27b9
44de95961cc70cf2109b01951478e3f2
8930e46553122ff4f3527ec437c8c4c5
bf4af57d8668f8a7f64538b3b5b69e28
ed196535f294b9b7e36ebeb64cf06a68
7dd011fc8fb66696593c532866ff5289
710b94a1accbb727e6fa96f75bde769c
f2468454850c605558c6e959e07483b8
cbf550e52f40c94d791aa44ab40d2e14
30f6d63ae1414f03d8cc48c0b8586515
4e4574bf57096ce027bc92366d0abb10
69c72e594f33f7d5ea82cdccc0222f26
de25f443cc3bd5ccf14d1b514e909bb3
0eee43e53dc9aa16e74f65ad09c5e82b
d9efe81f4a58efa16158a73b1449b803
9661df852aeeff9650fe8ac1a7412c39
5c7bfc85f733cec1370ac6ebbded4762
f7aeb4e1e0576d5a3d60db750282cbb5
1f542cf3e1a239f001bc0c421550ca6a
e35ac0d74c0c1e03b91a4c3083c767f1
02818a3bf4231a7a0a9ce6704a0d9ed0
6abe5757ed3098a45370453280b2864d
6eabc4a1ca7f4e62476a7a52c8be0421
8bbeae7c6067e2da6f5cdc232e271f8a
f41c55c4588a9c37a1ac0eac366ac289
b3af7dd2a66725fb34993083b1c8d005
d6c361f547a7c56c40791098cec92186
79c0cd43ee3fef2daf8c997ddb435a3f
867e462ffcbe4510e03db3b93d846765
4ce855d6e159db31376fd22b264018c8
51303064fdcc6f69898e9f20ed0dde74
b123fb543768cf6946b2be1e0af001ec
784a48688f137a570aad2f5e396f1787
ef75f86a924894fec1dac693d329a7ab
3881063f31833e97c6d3537c098b16a9
30dd0f30a35abf1e135932948d05251d
7fdacd5458f03ea0d20283c5d92a3c4d
1e81d417b57e45a9fc64ddbc64f0d319
420accd30315d90055d902b8e5bef7ad
90ff9d6855c24dacd066d5dce7542d20
70ba2bfeb8b9464bc04b1a27b4b9fd60
0e833ac74e16bb544f5bfbd7832a47f0
50f6f5e7eed54c3d981f33fce45bcfe5
7b97b9083c3a00bdd5f091909b760879
Registry:
HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835–0E21–4959-BA22–42B3008E02FF}\iexplore\Count
HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835–0E21–4959-BA22–42B3008E02FF}\iexplore\NavTimeArray
HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835–0E21–4959-BA22–42B3008E02FF}\iexplore\LoadTimeArray
HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835–0E21–4959-BA22–42B3008E02FF}\iexplore\Time
HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{72853161–30C5–4D22-B7F9–0BBC1D38A37E}\iexplore\Count
HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{72853161–30C5–4D22-B7F9–0BBC1D38A37E}\iexplore\Blocked
HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{72853161–30C5–4D22-B7F9–0BBC1D38A37E}\iexplore\Time
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings
URL Substring:
The best IOC to block if possible is this URL sub-string, it should cover the bulk of the campaign:
*.at/api1/*
URLs:
These are DGA generated so I’, putting these in here only for context.
http://cdn.arsis.at/api1/wHyH_2FnTTF7N_/2FhXZmgpmphwk5O9OziQw/zEb_2B5DYgJbfBIm/FmRcBJ5rwr4t_2B/HXDzf2JBmaOIc2ppRr/qOk29WI0U/RWYl44h7Rrdvl6JhfQ8N/OFsW75Gum2T1YmPxFqr/yjo7DHenOCjBP2mBm63lv5/3U4WbyECwXbT0/9e6lgvAD/El_2FKmWV2PoV0BgLYnYRws/aRd4jYbzWb/ZM0t_2BSzpSRmRuCB/_2FPSFD1YAeG/D46wvAmUzWs/KnDRq80YD12tQO/alOy_0A_0D61V_2FRPwnX/zjjvu2VNdMsl46tJ/d6hhxwBQSn7TC1R/0Rrc7PSIAtYNEjXuIt/ypAZEg2wW/B,
http://cdn.arsis.at/api1/Hmhc6xXo1ix/WZdv5_2FEhtQSj/8PneT9VWhkzZjfIVZm5eM/mVQ0wWySUq_2Bp2R/2EWTvs5RtU9bxlk/g0_2Fhxeii97r2IMwA/ZooXIKvwt/_2F3qJVEXtJSw6Dj5grL/xAWytzchh1JJj4f9_2F/ETVUaeGo6xh5uRJQAssVbJ/mOrohX5TK4pJ1/LB_2FYGE/CXifYBBINKa6whRC_2Ff74E/tzgKTZV9W3/nZunam8HGw0Z1BQgU/wgFTdP8YYCaU/bHtu4FoxCQW/xAe4S6F_0A_0Dk/qXp14NlqwkLr6kOGZpXeW/Mg1NQERk3s3ROcMb/TkpOUeO2/I,
http://cdn.arsis.at/api1/bKijOolxcMo7NabTdIGI/4rnFi4WcpLgfUVCRHHL/DS1ei6d_2BqMqo3PW0RzIg/IfKJ_2FZcTlLE/ZdhKt7_2/B4QTgYOJWt3gaqSgeB25cvR/g5DhguCskb/Dx7kmr7WY2EsnpVpR/_2BMJHC_2F67/9_2FFmeSW40/yFfXcgrVBQLnr_/2BlMtfg1LVQ2_2BjXc80d/3ZyZyHNKtB8tBXea/JQ3Ugvu9zCWB7vV/hLgKfPPsSLrqNE1So2/Efo5dILcr/bq2SDQlyWRnukJBKkBkH/_0A_0DWEqTi_2BHU7V5/froOJIHytaU_2F17jlIFNx/FSg3SghwNmiQc/YEVwRh9z/14RYiZHPNhEfDB0/z,
http://cdn.arsis.at/api1,
http://cdn.arsis.at/api1/g3cND3rYwENplG_2/FeEyhEJ2FAwkN5K/GPZSnLOBECVSYcCWuF/LzVChCMTh/H26ASmZUHOLPoY8ynrbQ/FRNrYU8iwT3YK0cl9BR/LGAfU_2F5h0R_2BotCubOD/p3IKFw_2Bce7O/Irk7JTqe/yGyWmV00k8YVCGGyfJEJKG8/H_2FvsyRm3/2q9IylIe6q4fCTy0G/hnBfQauMcYZ9/q3CHw1P0Ozi/ZocibPMI5ZuJF0/TaaBy60OrfcaLuykZt8KZ/lOxXaJeV8HJuj_2B/_0A_0DTkGCK8hA3/o8nAY7GCNcGLSoeiS3/F6RCjPYZJ/AbxIhmzI71rqW6Rr19i0/cBfLlde1Off/a,
http://cdn.arsis.at/api1/7quspzaiotqt/kyl_2bz4b1j/rfygo2qzb_2bam/kdsiikjgxwrydnaudlqlz/kw6ajofjr1u4rccg/qzqkubzbmq0gvwx,
http://cdn.arsis.at/api1/KptPXBVePWIw4eofz9MO1/K7ZRymXNuXRiFAEN/Kl_2FZTj9JanBu_/2FZjFImrYcR5hM_2BS/1H_2BgfMe/0BHr6BORQnpEGcLIWTya/_2BUosMraCW3a_2FfTQ/18cMs_2BvbGVAR0YPCJbBd/81yRl_2BuvXcu/UVrVbN7X/AOx9_2F3JoB3q2G_2B1Bn67/1czsTyxh1l/x3i1pRQBkW0YrP2sc/4OC8p9gKWUIS/NyaXgPFjRdL/k1fTQneeKYLOse/PS5vaOs1qquJDzKuESe_2/FL_2Bla_0A_0Di_2/BkhMhP2Hefn_2BM/GNyQPPRgyDIGh1XtHG/ub_2F85LSlny/kBWvw,
http://cdn.arsis.at/api1/l2lqGv4pzkol3DfkaaG5r/fCBE8ZFyEf_2Br5X/YOPMxsMWm0eEWgL/wXM82u9kDgWKY9KFFb/OCGZZQlP1/p7EfQi_2B1FuSC2d53m2/LIPoVtvtZHm_2B_2Bs3/UkcxJpDrcVgEVZdFBxlvdJ/SYVKh3_2FYcHr,
http://cdn.arsis.at/api1/EuwHWjjfklD4HW3/QOQQuWhTLTmMqf0I1t/gDDgSFwLa/DgWGeAQJTQZhYOVSzAae/bR69K8k0iA2TW4XXHD_/2By3S3sN_2B58Ztq2D5JOg/OgN9dPC6QxUzy/oPSesze_/2FIH91ahxWLnt9nDEQmzeP7/BoVh0i59OP/kDn_2FCLEpFjhQloV/gEMGvuzPcwcE/9KJ3PIOmJf9/XKNGi0MI6NUKuo/rUj_2FbYFWnRqF1gYyLWZ/uku7t0fb_2BoDgf3/hlf8NYl_2FOsBlE/5ca_0A_0D8TdaBBcnP/apRDXdeUZ/DxOzuK7VpGChB5n0YUuM/uqg0Xg16/D,
http://cdn.arsis.at/api1/xAoTEveG1GOmkrm/nYSMTm5K_2B3ivk_2B/aW44uzDni/rGzenJoOsx1ylMpGj8Fy/Ho823Z4Bu0n7YRE2QWU/z0Us1M_2FIJVlBamzqU2Kh/i1wwt8vvbpB6a/dm2GR05Z/9KqZXTZd8v7XB_2FG_2F6DD/zFGS7m_2Bd/JNy1kcVdehBGp2K_2,
http://cdn.arsis.at/api1/H_2Bh9rCYsD3etaukrm2/RByHpyc3FDpPSGayeJ8/drp8H1EloE0ocNfSkTyxXI/VvIT3FdJg_2Fw/DFjkaBgo/GEyHIuh_2FFnjWDxWD4Np29/0UgJk6d3t7/3VcB7hvzYGOlFAY3T/P6MfgbkM_2BT/0WigD_2Faan,
http://cdn.arsis.at/api1/gUTsb0hTss1/Co2YYIgdYOteWU/qElHYaEtD_2FWkg0zjGQ2/azHRBwmvRKDPyCrj/D1fNAUBn8aAII_2/B17rzY3VvonNe62I0i/gKQExqmSc/urvgyI5AxQFOZMU_2FxL/cs8jPxUpVtXaZHLPbeO/UpwAyJMMtjBITDKC6mWy8D/0sTnWn_2Bp_2F/svO7Pm3F/cAuvsuGx_2BSMPB6H3AjKM7/RNgNcYtMhI/MDedJewNrSN7tSzn2/7ao4QY5kuC2e/3tLKFEDYr71/Pdjrv_0A_0D0ey/GxepA6s7QXvU1gNk49z53/taRKvSQ_2Bm03BzZ/dMFt7RKxAssuB3_/2B8aRxxGgc9HM_/2F7_2FS,
http://cdn.arsis.at/api1/cVkjL_2FgOj/Axtod6Fmq1M7uV/HP0LZhtAOgdOD8Hyaxj3J/X5taQx9wI_2BCzAV/pc2nDrG3bK0BhUY/84vnlg8tiB4aJeaiaU/k7gQ9CNGw/0NIkgfVHBeUgBKhXyB92/2FB6A69Vk1um1xU5uSJ/c792Et5pbJa3aOdwJ0p0po/qmq0L_2FJ90Lo/Klrbh_2F/PMO_2BbjEkh3Z4FNxKnuu7Q/srYEOcmTwj/C2Yr3isfCqZVkdjYO/Gw_2B0W2bcM3/fb7b2Gzely3/9mPjM_0A_0D_2F/uwVTC1CQpODOXTpmqK8Ck/bn3tSWGSv5Wn8L6H/IpRy4n_2B62CRQ8/E1_2BsIMKsG0J52/XWY6,
http://cdn.arsis.at/api1/IBMv6_2BCok_2BLpBpO_/2B9v3Qm4_2FX45_2FeO/BcwXXX8AVKX_2FSJ_2F3B_/2F90ZMHaYC8V0/gMtHQcL8/8xhQYBzptqhG6xGG5MnQop7/oIKbRstDx2/ExsBfINhuxanKZFXE/KnrIYgK72mLu/Nhh7QRPDtmE/Ql3v_2F15M1DyU/KMb4qYU0ZJg3kDW0EVYOP/n8DViUy8bQ2md5x_/2F3miyEggOO6caB/KHIat0tyrFmCjM7drl/0lQK3sqka/I_2BknPWNQDkiYX4SRhL/Cs3yR3_0A_0DCeA_2Fl/uV317Sm_2BnBkgDy5I_2By/sgpD409c3SjVY/1gTqOLuTi/Gq,
http://cdn.arsis.at/api1/fgQ1NTCojxJDwC14E5DnwCl/KavCi1acDy/e13B21vM6MhLM4AIK/3f3Mi2QxzHgc/P0XZCdOs1js/5fN1p_2FTDkgeU/AqUspf1hxRYlu68ujw3Pe/eCRlyC8QVIeppr8e/a3LTNC3EgnQJJIg/ciTQIx5FCT7KZJE1Ff/AVJrICtFy/nurNyUJcnHY_2F9q0MDo/MGn_2BG_2B1nHgrdTm0/_2B987cwrjtPtwS66PVHbh/o8IjRy9qG9Ol4/dL6ml6vL/Y3ZwNacBpvDTGi_0A_0DBkU/23TbrUP6U0/Fe_2BNmlZHVoqCma_/2FNYDLvgmazPW/piXxbg_2B/p,
http://cdn.arsis.at/api1/D2rtQw08vKM582WflpW/p2FmjhrjHMJenlrVhtAhxQ/hFGnSj1viaIep/SIxkDt2S/sSxf_2Fb_2FBwzYcEusQ7V_/2BmZ06zkmD/cHZONKEa8k7gtn824/z3pddkMEA2mw/rv1fPuxtoCd/Lwd9ELm2_2BRoz/qw5JlhPgxBzAnvqhG1WJC/HA5OEDW8OQ7aTUie/flCMz0pmZZ04Sj8/46KMFjhzDwkS1hTLic/5rofo_2Fj/jnU6iFZxQB_2FO64LTy_/2F069hpwXWqJlXOPGm_/0A_0DD60lXqiAmm3V4jxA4/PqAcIepWivyZe/rzLljDjj/l1upYnt9s4eRpGifXgmdu_2/B0C5qFD0/5,
http://cdn.arsis.at/api1/vmiHof0LS1v/Ku1jN794t4oF3a/njj1yuBR0Dt8TVoLZTTUp/bVL1a8e_2B2qVXAd/rTfw5jO6iECEV7V/YpYOTs77fnQLs8UGk5/5tJxWGoar/QMybgx6cC7KfI7WJ2f0N/x6csvzW1tjK5n_2FoV3/WsTnRaPQj8nSQnucyQywfI/LzIovV8M4UC2f/LCzJ3f_2/BO88mmLyFXc9Nc6TwIsENlQ/xUFaYoaPk5/ksi2PLXcsU9UzdfUm/12kea_2Bgbln/8uaRMCYe0uN/w_0A_0Dc0WjVni/TTg3jJjg6J39vvfi3R5rp/Dmfs78qZwvERXrkY/XweDtkEMkpm7swB/n8NLacqV/p,
http://cdn.arsis.at/api1/WAGKecAj9Dbjs/7eV6fbXP/fzQ59RCdM17G9RqU7jWJvWm/sRRz9tvx61/C10gkyTA9lbvZjzdG/mGXGz8LelSla/KXZARkBTYFs/I4W2fC6B11VUEO/_2BbiIrbKNJ3E2uSuJW0b/Q2TE0hpht_2FeyXy/fACOaP5YJl5ETaz/pTrXKS5D12K21UpUnr/_2FPe2pQR/ElhIrGDkhd9S2W16Bdtt/yAISY8HXBtlYk8H4ykw/iK9H0s79QmQeldXdnPLtJH/JudUVjihx_2F_/0A_0DfSf/iD_2BTrJtJB7BfLjB61x_2B/E_2BhDMyt8/e9EzbR6r7apnpmagh/n0i6CKMvr0/mBDZH6BU/2ZW,
http://cdn.arsis.at/api1/7quspzaiotqt,
http://cdn.arsis.at/api1/yPY5GzJMXeLsnFQcULKL/M2xm0HOTahh6MI7zqaV/pU6AnHx2sZyMM_2BlFIOsd/aNXpV8Gm2fSNI/bdrfXDQ3/siBoMPGbqE7ZPvMJi4xFA4K/Ur2_2BExc_/2FIedCJ6vqyKzlzPJ/O1eD1Yg98B5k/Ai3T6Lwj67I/EghyQxbzqm3fDT/AiTqFoM_2BumZl_2F0u7_/2FloFnIdmT905zt5/JMSZTwwVmBthSw8/O4eI8xXJgwvGjiOg_2/BbqQH11vk/m5l775bVniefLLWdv5_0/A_0DB_2FeQGD38puxA1/beDfbikke3CZNq6P_2FJYe/Int4ViToLl6Is/p,
http://cdn.arsis.at/api1/NlCQFOIF5RKo0fNM/wdxpwV2dHN3JvIt/ZE8M7iIF0R3GfMTcil/7HuauJIOy/oC8M61BnykzaA8dCVpBg/9fIti04JA1wUU6Eh9RI/QA_2BSLCgulYQ4HSF2iWDJ/og_2FqZv5t2GL/bpJs7l3X/59zhZVLGEvqHzLdeUNsBaiK/Pt33026oTu/l46HbgzEQUNK91JF9/fi8tEwNCrZGO/uWsBKQhc9TV/H0t9AoT4s2SHr_/2B3ZPR80sQXab7ZTdzmYB/_2BiDGlsTvbI_0A_/0D6M7425x2RzQHO/lOtvREr6ZvdKRaw8zl/81tP7qMiv/xriKAWa,
http://cdn.arsis.at/api1/e7lXH69k5zpthIR1/f9kqN5i9Ck5iuSz/_2ByNUtaD1rDn6HMsv/bIFXaYH_2/Fu84pXWv5CavXOTyFNSk/1kUVRtSRjPURsuAnXKA/ux_2FTcSDWBkqN7sUmwVsR/DlU_2FcudLUmU/b4bsYIXs/N1vJPIQ_2BN7GGtdK0m3WJ_/2BKU_2FbCA/inK_2FJGBxR8P5aR_/2FLJ0TQl4IQh/OtX6Wiruc30/RBQwA3nmqia1tS/ANDh6jiHPUuq4vAuWPFar/fNalJwstRUcm8HqJ/DvJ6GT_0A_0DtQF/WA57L_2Fo71zlqkStG/aamwFDP9W/IV93ceYB/y1VLAOYFg/Zw,
http://cdn.arsis.at/api1/CvinmSSvODDZkdi/WXI0RTIaUCxAhJjBMP/IIPB_2Blp/txN_2BNWI_2FIqSsPuK5/eOrsWlwg61vbrpeZwoF/aWZ6q8jNAU3H1hc2G9im0d/JKSptNsFpJSFh/B0u3bJxz/0dm_2FsPsuIgNb6AGiFftF8/wnvZFyk3Ne/pgE3xGRzUP7E5_2Fb/UNZ9g1llD4Ep/VoFHYpB4Fpf/aRYFT8Ov_2BDRT/pF_2FUrK8YFUhnSUN5QIL/3DpQdnnc6yjVFY4G/wlDLTQIBKMkVQJ0/Uj6_0A_0DNh3ggNRIT/E5S0MwHCs/kmTHI05_2Fcc1P_2FIcN/Jxen8SiXps7/z9,
http://cdn.arsis.at/api1/0QKQhv1lfODyyt_2BrVQ/bob1P6_2BI0ExeXGd58/VR_2BKrJYiSBk7c8rwACur/gl9xIc2_2FdsG/_2BUzWzx/_2BdWdnQ5HqO1QMLdYvz7OC/yIrpaA5vE1/PipnQ0qJBJnCvM9IS/7Eb4zgBJj_2F/nXl_2BdTAu3/Ge1VuCdq7QwCT1/7vWQcMySe5vuTpblYMQ12/JXIWNPGdDKbUZhuq/V5oqQcSm6XdAnr_/2BMbUwzqKZvZynUwYX/bjk_2BLgD/NFBFIO8fejWITW_2FnbC/yWzXCl_0A_0DuYT75vh/2QUdBD84qXhIVRcf5TIVS_/2FAHAB3E6Zb2S/hKHMRdWL/YmIV2rIAhQoSWLk_2BN/fVh,
http://cdn.arsis.at/api1/H_2Bh9rCYsD3etaukrm2/RByHpyc3FDpPSGayeJ8/drp8H1EloE0ocNfSkTyxXI/VvIT3FdJg_2Fw/DFjkaBgo/GEyHIuh_2FFnjWDxWD4Np29/0UgJk6d3t7/3VcB7hvzYGOlFAY3T/P6MfgbkM_2BT/0WigD_2Faan/MlhOD00QiZEAfn/dgbov7h8bjDFvjyPoft3p/faRBmPMGdyUZdfS4/1bzvSWlqKqsUlC_,
http://cdn.arsis.at/api1/j6mW9lD1FVMRxXSjvK0f3/djuTybikjF9pGuGs/xW5bTMUWxMhQ0op/OC8i6YfxaJy76FywQK/XO02QoLgr/_2BEMLgDyfBNQDFaVxL4/xEu9hYfCbhVOppruX6x/_2FhAiIQhdLnq7ge_2FkT5/JCnTv99z_2FdL/JDy3Zw0z/wV1hAocrNn4_2FZp4KFexdP/bNfMvXELkC/wu8h_2BvF_2BC7jQp/YWQ_2BYmFkFp/gmdhRxxw6mp/_2BSez3DRvzZaH/NSzlmPodKrrO2MD9xA7AG/i_0A_0D2ZmT5jJcG/iTAvoBbcv_2Fxis/_2Fco_2BwMpyW0GqqN/wvmRzy_2B/nK8ARuM1V8fyvtNxGeV3/xT5VS,
http://cdn.arsis.at/,
http://cdn.arsis.at/api1/H_2Bh9rCYsD3etaukrm2/RByHpyc3FDpPSGayeJ8/drp8H1EloE0ocNfSkTyxXI/VvIT3FdJg_2Fw/DFjkaBgo/GEyHIuh_2FFnjWDxWD4Np29/0UgJk6d3t7,
http://cdn.arsis.at/api1/5zN8rGv01dngHxTUFmR/2JFBCSlIZXxJJrgccwAuWY/5UqzTIh0fjIyB/sUMkLbE4/perxsUm8IpJ1X5elG7FsWyi/bEAn52E2U2/Ne8qpkLARu_2Bezew/8bqin17A_2Bm/ATQ3eksSu4m/e4LRItiXra1F2v/x3S634_2FcumsHiDQDx_2/BkOEVnvF5wohZpz7/kvzCeFagfNsncgj/P3mTkM3G_2BlZzrXpu/boDwGJeLl/5Wi4xwfiAo2XoR8vutkF/Dq1lnIP34Q4N0n_0A_0/DYucJC2z1sUeKrA1A2OIwJ/8yRuHWTCHQURO/PSuSFIxgS/LoOm,
http://cdn.arsis.at/api1/g3cND3rYwENplG_2/FeEyhEJ2FAwkN5K/GPZSnLOBECVSYcCWuF/LzVChCMTh/H26ASmZUHOLPoY8ynrbQ/FRNrYU8iwT3YK0cl9BR/LGAfU_2F5h0R_2BotCubOD/p3IKFw_2Bce7O/Irk7JTqe/yGyWmV00k8YVCGGyfJEJKG8/H_2FvsyRm3/2q9IylIe6q4fCTy0G/hnBfQauMcYZ9/q3CHw1P0Ozi,
http://cdn.arsis.at/api1/aEv1VWdHo/5XsTxwxgNxjOzoqYpJ8g/fLYR67E_2B38uvZEYnm/JtKkT5VISubU7di8NfdtCb/C3_2FsmGqQNkX/x2fNfAmU/uCYKmaYgF1X3CGhtAkUkJyQ/bL8OZhFFvK/HwJHWlk9EGWWSCPKM/su2cQgHw2jvx/WrI1ucSptCJ/cXGY0ElpYU7x9c/C8f83XRuRtSbQpSgQxuHG/WxoH_2FspSQKoFKd/Noyo3XSCngMDBVF/tPpjDR_2FhJA8HPdiu/9IMPBB1v_/2F2YP_0A_0DrbLjIfshQ/7JWzG85T3fUtmBMu2d5/fGoCFUMQn1ohP_/2FBBIDR,
http://cdn.arsis.at/api1/Jc9GRErJhjX/sp0eY_2Fz9sMoq/INfGiH2aoUpN2utlWNAlT/uUP3Nsq5QSBTWnSo/hgkBlJHjuQhVUOO/JKQzOrlt3mUOBxQh8Z/F9Lq74Ghm/PpRsRtNYm65dL3aQZ_2F/hrdB3svdy4r2Khk_2Ft/dBwg52QkZNGC_2B7abVx6Z/BF_2BgDDRTVQr/fIbKM3hJ/LbH4_2FEnxj1dYYbApGpsBm/KAHhq3TV_2/FNHIfw_2BumlEWvVp/U_2FgLDxvU_2/FMMIVOp_2BC/BTcnGtXHhDA4Uq/2_0A_0DD1tqOjYUs61ilO/wKW7ENIZNEdLMhcQ/KqqPwuutjCi9oY/zr0,
http://cdn.arsis.at/api1/LdoC8y0TLbGdp5uNO/okN1YRVKJ_2F/3tqgLpdrfys/K7SOMU7v0ROu1p/eWodB6Xn7vym8WAlxfwH2/UOcQ5zwOuDKtb_2F/DP3pFl7suupEFMR/J2PLFV_2FmaW0ZUppM/WIGhJcRQL/l73ASNxP1kLzrAdSECeu/pxzXbX_2BsNBW1oKe_2/FiAMKl0sga5MZLagAk1HPj/gP3GgbPkAZCGk/T_2BVHya/iPB5PcPEfYQAhCrMH97HRxC/poPQBcHm0L/_2BhGQ5n_2Bee_2Fv/0P6wz_0A_0DT/BSaYLyqgyAh/feCenWbtIGHT4y/2w7V6YrG1paOTFnaypMSe/Qe3ia3m4x_2Bke3ZqwwTd/Tc,
http://cdn.arsis.at/api1/7quspzaiotqt/kyl_2bz4b1j/rfygo2qzb_2bam,
http://cdn.arsis.at/api1/g3cnd3rywenplg_2/feeyhej2fawkn5k/gpzsnlobecvsyccwuf/lzvchcmth/h26asmzuholpoy8ynrbq/frnryu8iwt3yk0cl9br/lgafu_2f5h0r_2botcubod/p3ikfw_2bce7o/irk7jtqe/ygywmv00k8yvcggyfjejkg8/h_2fvsyrm3/2q9iylie6q4fcty0g/hnbfqaumcyz9,
http://cdn.arsis.at/api1/g3cND3rYwENplG_2/FeEyhEJ2FAwkN5K/GPZSnLOBECVSYcCWuF/LzVChCMTh/H26ASmZUHOLPoY8ynrbQ/FRNrYU8iwT3YK0cl9BR/LGAfU_2F5h0R_2BotCubOD/p3IKFw_2Bce7O/Irk7JTqe/yGyWmV00k8YVCGGyfJEJKG8/H_2FvsyRm3/2q9IylIe6q4fCTy0G/hnBfQauMcYZ9,
http://cdn.arsis.at/api1/g3cnd3rywenplg_2/feeyhej2fawkn5k/gpzsnlobecvsyccwuf/lzvchcmth/h26asmzuholpoy8ynrbq/frnryu8iwt3yk0cl9br/lgafu_2f5h0r_2botcubod/p3ikfw_2bce7o/irk7jtqe/ygywmv00k8yvcggyfjejkg8/h_2fvsyrm3/2q9iylie6q4fcty0g/hnbfqaumcyz9/q3chw1p0ozi,
http://cdn.arsis.at/api1/SAAcuzOpfbMUoAhiH/m_2BrMu0SH96/skxXB3ysNuv/HBD0yGYmVf5D4l/jTt3m_2B7J75EKo8QDZh8/utk5MDA_2BNEhYQW/qfCxO_2F16dFGxJ/83EcrB8_2F_2FBIVgj/9EfwnjiEj/33x5XSl1EpCeDE4Ofi2t/FSiLqlmepy21EArIhHo/Qp7ioENXTqcg4Qc3ZA1Sku/z7vvgUpTVyynY/hi21au3W/d3nXIl0iL_2FyIP5VanPEnC/jMP69Vnmp7/7oogSQyVg8rvJOsjN/o_0A_0Dmm2vt/VA45mg_2Byj/CQ4z5gcNmGQiLD/nM9wSUl2UXXolMP2zstSR/vCgZb_2B/tL7T1A16/gqCwp,
http://cdn.arsis.at/api1/wX7K74Uxk/SNf1bOzWWC_2FrfBvEV8/t3Umjz6iuBtRPfEDzJM/pto5_2BHY19v0WRY89k2Ue/Lt1U7vOY37AP0/GBJC3_2B/ILn4wZND5PlTV7Fg_2F4owA/u5dXUetqgZ/QrKVJsWHynReaGbWU/OSbMc6qqm7pk/6SQJCxk2BSd/it6alsxsnAYvhP/IJJ5P865h3zAoioOaxoIm/b2l5WqhSwhWatAA6/7YsmeGKCRJ5CYMk/tCH5hcWzrV_2B5oqrT/q3FjB6wXN/HULrE_0A_0D_2FzY0NfV/H_2BMcfF0jR2l_2F_2F/b3aA37YfS6RPmQC9APnxrQ/GBgTTkSMghRCZ/ArbbUhdQ_2/B3GXy,
http://cdn.arsis.at/api1/,
http://cdn.arsis.at/api1/2XdbqrGFM0J/zprSG103I4Jpnq/QodM_2Fb_2FAMY7mtlRUh/ZSlkOCmTPtrqFAO8/E6oZhqiq_2FRVyn/VoEfaka0YEykKS2CjJ/giPfTiPS_/2FUQYD7o50spr27pL4WT/3sZ_2FFHQ429Or63ypH/ClrZuRn7BizsaPp_2Bz_2B/cSLt0McCk1Rpz/bHghq8CR/RKtdCEJ8zMebfSqg102aAq_/2FFSsmJiEO/phg_2B5faPoUyc3T1/Obu2f7ad7pmX/T0y30R1xiaK/vPAOqbfRR_2B8_/0A_0DkjonO_2BwrlxPaoL/IiYhgqvd8KqsCNyz/OAGlUVBvRlPP2/heOi,
http://cdn.arsis.at/api1/CGmNKJF1rvFYA9SPcsH6O/pJLsQY3Yzmsa6JsT/nE4s9mzNA76yQSR/OIxmBhVsIReEYPZQuH/jNm_2BJ8a/LRAN5qXNUVeJ9L88ID7u/t2xX3HseBfllz7uK6OL/QOzShacSeXOMV_2B1Ig6HY/Oppvr7Rub6ec_/2FEXXHNa/g9cVjN_2BrUTpxt35FDmbXy/BEnVolKAvJ/OSWS3JR4GnbqBqZvG/4HW_2Bxo9MPk/xJiza230_2F/byHduBjraY10ka/RG5fpqfuxL9qvMbw_0A_0/DrZqhxe84t4nGyDQ/8tJjbR8EVE1iM3w/rE5sgUfdlfWMFP/lU1,
http://cdn.arsis.at/api1/oF6pYWXWnp3s7q/qSSOLKYW_2FfFVcmfQXrS/81vidnxgw1SLkB1O/hNTt3eBVPieCJ0L/IaZMzPDIYnA1B_2BHJ/5lMuNx_2B/R88RQSfSZHrwUkH37hEH/ko3R_2B1vKM9pEZ_2Bq/O6bameDDetTdx7Nxdy7ojN/jK_2B3IBdcmFr/K2lfa63s/ybr5H_2FyQnB1Hs9988JESg/_2BQuvc_2B/nGJXDpP_2Bcz_2Fqf/CXe2oXNqmJUG/BD7iJ1tB_2B/xry2wzMXLP1zcY/dUQOdEqOO5Vbqz_0A_0D6/JtWWqX9KNBkLeuPA/fYGqzmb2YoUWChI/IbOWAuYWIssuH9mPlc/lrbD_2F0oK9T4N7Cg/9Px,
http://cdn.arsis.at/api1/g3cND3rYwENplG_2/FeEyhEJ2FAwkN5K/GPZSnLOBECVSYcCWuF/LzVChCMTh/H26ASmZUHOLPoY8ynrbQ/FRNrYU8iwT3YK0cl9BR/LGAfU_2F5h0R_2BotCubOD/p3IKFw_2Bce7O/Irk7JTqe/yGyWmV00k8YVCGGyfJEJKG8/H_2FvsyRm3/2q9IylIe6q4fCTy0G,
http://cdn.arsis.at/api1/HC4EMEGb/ma9_2FcQMbbE1MEUzuPhlc3/HuxtC0ELL8/gBggc7AQN095TJAZc/yJbBXh822ZwJ/4D3wa4fw1VR/6dHNEU1AY4TUze/uvosZ9c_2BGBrZrzsEaco/OkQee4udEsoHtoMM/9hyBVbBE1H72ZMt/EkwJuv4X_2FONyycJh/x_2FfNxUn/s30OxSp_2BFg597AbCSL/8KAdjLGmOp9yqDHaQCQ/3WimhevROJGCxmrRm0L_2B/T4KBbktwcI3B4/9FQjh_2F/12SJJHpXlm_0A_0DPB9M17V/tJMnv2x9o2/pL_2FKHzb18qVhESx/NzcDsEYyA9Pl/AQkvOVSJ_2B/iXevhwna/Eu2PXQB,
http://cdn.arsis.at/api1/zjc0OHx1dxbO_2BC/Z0W6WHf02Tgr8CF/P6U6VnRuAjgYgS7YLl/FKWxx80Ml/m_2F3_2FbtlG7X5iGOos/BGqdSnbysJt8NureDe6/SMFedDNy1ZDCYM1Ph_2FA1/kTdR2i6uDKLsz/va_2Ff7n/9FBjRdQlELAERLLowzmvuFy/YqZuzV_2Fb/fcRT4rLypEsqFq_2F/tToj9HStZXCy/nWIKru0eVPP/X5mdzNGzRQH2Gw/ocgxY5HzdKtDUL_2F_2BY/DFi6dYsYAiPDG7_2/BCX9Sqxh_0A_0DY/ESpN440a5SC2e8A6sN/k3yWPiL_2/BYj_2BKrmS6Dd/8JAJLIW8j/M,
http://cdn.arsis.at/api1/Qi6rv8BTou3kF/p8AxlriL/Ya3MJ5FwEFHIHKYUX2HQ3Kn/PiXWBJwwZm/ZQDDwA7DtG1pu3AnV/LoYihqMZCfjG/tccd9zjTrh9/VkmuC1dgyzHC7O/2AkJeF9QL5Zz3CBFSdri4/gM_2F7vl_2BbYDAc/4kAvDjXZnWMlyL8/uJ0jV4dm65bJII_2BG/wO9NgWoZo/9LyYogHd1fEA7zqK6ipK/bfdHL8JvaL9BcNDZXM6/Jwtg0kTS2Komghqd86NM83/ML_2BcMcF5st_/0A_0DV3D/khxzhVG5PUkdgxT0fFF_2FG/GMuxdv_2Fz/FVpl70cp/sBm1PsC,
http://cdn.arsis.at/api1/tiZ1bgzLeqSPe_/2BbV_2FyzjxDJmEF4N28s/qmyqmpJjFx9rJgpg/VQkGYSc95fwf8cB/7G4SBIlQL3eMR8gt5C/5JyKg9wk4/I_2FMvNHcQyh7U2aXpNP/g0PRpP0sgNajM9N3qz4/Taiy1PVm31dNAaYIXMfaJo/WtFupMfWDBHgg/uOiZBjFt/7cmXtNWpMm_2FAPDPHcqzyy/Y1K7H1jGmt/hw8EyNpiL7OjDdLzw/TN4sRda2_2BH/QgjM83An_2B/6239F5Cdnyl1Kf/Si_0A_0D48gPk5znWQKjU/0e6c1i0PHqBAaYIA/e8tfFak1wSlstEC/sT5jczS25ic4GIJ7GA/_2FFJ9Fe,
http://cdn.arsis.at/api1/x3xoabxfe/m36ha01qzso_2bjhudn9/jmn_2fxzecqgwytustu/5qxbtdfibvfa3ipd71sin2/oamfzefsrxyb2/7f_2btbg/f_2bc52n9v4gquoyxqias0f/0rzevykjov/jaqxyju11o1bhncek/r0gceozog6hv/dmzflcjz4ie/ugos9qqpnd0r_2/fmdz644czpnik9nch8dcl/zgwa258uymp0i1vf/hduifklx7woj2sc/gwpnnb9sulmtz9576b/oql4_2fzh/nslgpjj_0a_0d3al6_2b/yasjc76q2mwqxdbbfzh/n_2bydnxi04kv3vi7fzr3l/iqv,URL,mitre/spearphishing-link,ursnif,vbs,
http://cdn.arsis.at/api1/zb8NtR0AhxP3f6S9VBW/RWPIgzxOtEj4nbciJA1qrq/NBo_2FvVgRVRO/y_2BC136/WXmjrLxAWby648dJ0tmlI4i/1kW0E6M8uc/_2BKFbi5LiqIj7c4S/3DZTwUYjYhSe/icCsvQKK9uE/C278p4q0UciSjS/4qQsQ1S_2FhIjjGiKNqA9/thUcrJSW7STH3_2F/_2BcuyuzHmESCmd/kzLP9cuY_2FWXj3ytV/V5CDV3m4J/o8oPpD2I3WTnwEm8WGRp/mgGEoArvFjdKUssTPx_/0A_0DUZnTXFaWPU5qzLGtB/gKm9JMTWRHbmj/4ox97_2B/lymTmPns5wc9hyE3aRky9i2/apXjVbvu/0,
http://cdn.arsis.at/api1/mbMl8_2BI8RGm_2BaK7yDye/1m1qN1n6yB/WDap0lzqbLndOuzgA/eMgDM_2FSRfU/7Nvkmt1i7Ov/XvudlCwAWAjW6m/Dzbl6ue8hwKBrdctpqA1m/o1PKDVx607XkFqiy/WbaCh8Q3k0qy4y_/2F_2BWqk8PcC_2BADM/kjsmq8ne4/OoxWB8C_2F8pvWW87dMD/a_2BhRYTioATke_2FIU/Lw7iXdJMIM0kXLnugkmm67/2lVCQAa7bRosi/aWdCgykn/N_2FlTFN9CHiCHOUD5MUw_2/Bti_0A_0Du/Z_2B0IJslpALq98la/Ho_2B4D8O_2F/js_2FDJ8Pht/P_2FH74IBC98hK/rA,
http://cdn.arsis.at/api1/fbhiiqtva3mmvkocd0y/ygykeoaudbvbiquy1hukqk/qjmuqtkaiicfi/vanyrf6s/6ydfg7utns_2b6gi0lbsdxm/dfaz00gbo4/y_2bbxbajmmnmyn3v/vk8baalp05oz/rc0hqza9jlh/ouq1r8f5egg6rk/6lc_2f2zijt7bxwdvfdun/y5v1dw6wsywea4xk/odwnnhtxnpvbwk4/rpteapyd_2beaq3qd1/6mrtaz_2f/d2ufo4g_2bl188tqoqhc/dcspif7ta5lsaf1h_0a/_0d9ulxux_2fue2m6klhft/uztkkc0futwfk/5qditm5g/m8eflsjhwed7jk17gqscw70/eaf7leu,
http://cdn.arsis.at/api1/H_2Bh9rCYsD3etaukrm2/RByHpyc3FDpPSGayeJ8/drp8H1EloE0ocNfSkTyxXI/VvIT3FdJg_2Fw/DFjkaBgo/GEyHIuh_2FFnjWDxWD4Np29/0UgJk6d3t7/3VcB7hvzYGOlFAY3T/P6MfgbkM_2BT/0WigD_2Faan/MlhOD00QiZEAfn/dgbov7h8bjDFvjyPoft3p/faRBmPMGdyUZdfS4,
http://cdn.arsis.at/api1/7quspzaiotqt/kyl_2bz4b1j,
http://cdn.arsis.at/api1/AEApm14UVcYD3SWDG/favicon.ico,
http://cdn.arsis.at/api1/l2lqGv4pzkol3DfkaaG5r/fCBE8ZFyEf_2Br5X/YOPMxsMWm0eEWgL/wXM82u9kDgWKY9KFFb/OCGZZQlP1/p7EfQi_2B1FuSC2d53m2/LIPoVtvtZHm_2B_2Bs3,
http://cdn.arsis.at/api1/An0vCmUtPCRvXWxDp_/2BCA2e_2B/udkfSPeU879CSlL_2BbK/30ffSOza391MvNrTxzI/FQPIyJWbmEl8dJFwvATf6P/_2FZfSBc_2Fn9/aypndCKx/lXwyoTLv9GuS2adT_2FfPLf/sReEHiOSIZ/r1sCpzFXho_2BhP0S/PAQdhVP46YwP/npD9cR_2Bpi/olFBOJP59DUtfq/eYawCS36NlTMtweUDU3xM/7GzB0ocL9eCw2Lzj/TlL1WbaDDMZOukY/6XxeOvkQd_2FFpvjFb/ZtP8_0A_0/DCyYn_2BnOP7Lb2fKARJ/W1H3tD94f7BlGgO40Pf/X52wGh8b/CaI,
http://cdn.arsis.at/api1/l2lqGv4pzkol3DfkaaG5r/fCBE8ZFyEf_2Br5X/YOPMxsMWm0eEWgL/wXM82u9kDgWKY9KFFb/OCGZZQlP1/p7EfQi_2B1FuSC2d53m2/LIPoVtvtZHm_2B_2Bs3/UkcxJpDrcVgEVZdFBxlvdJ/SYVKh3_2FYcHr/VX43MlN8/XvYnDOIgdJaUV2,
http://cdn.arsis.at/api1/7quspzaiotqt/kyl_2bz4b1j/rfygo2qzb_2bam/kdsiikjgxwrydnaudlqlz/kw6ajofjr1u4rccg,
http://cdn.arsis.at/api1/x3xoabxfe/m36ha01qzso_2bjhudn9/jmn_2fxzecqgwytustu/5qxbtdfibvfa3ipd71sin2/oamfzefsrxyb2/7f_2btbg/f_2bc52n9v4gquoyxqias0f/0rzevykjov/jaqxyju11o1bhncek/r0gceozog6hv/dmzflcjz4ie/ugos9qqpnd0r_2/fmdz644czpnik9nch8dcl/zgwa258uymp0i1vf/hduifklx7woj2sc/gwpnnb9sulmtz9576b/oql4_2fzh/nslgpjj_0a_0d3al6_2b/yasjc76q2mwqxdbbfzh/n_2bydnxi04kv3vi7fzr3l/iqv














Comments
Post a Comment